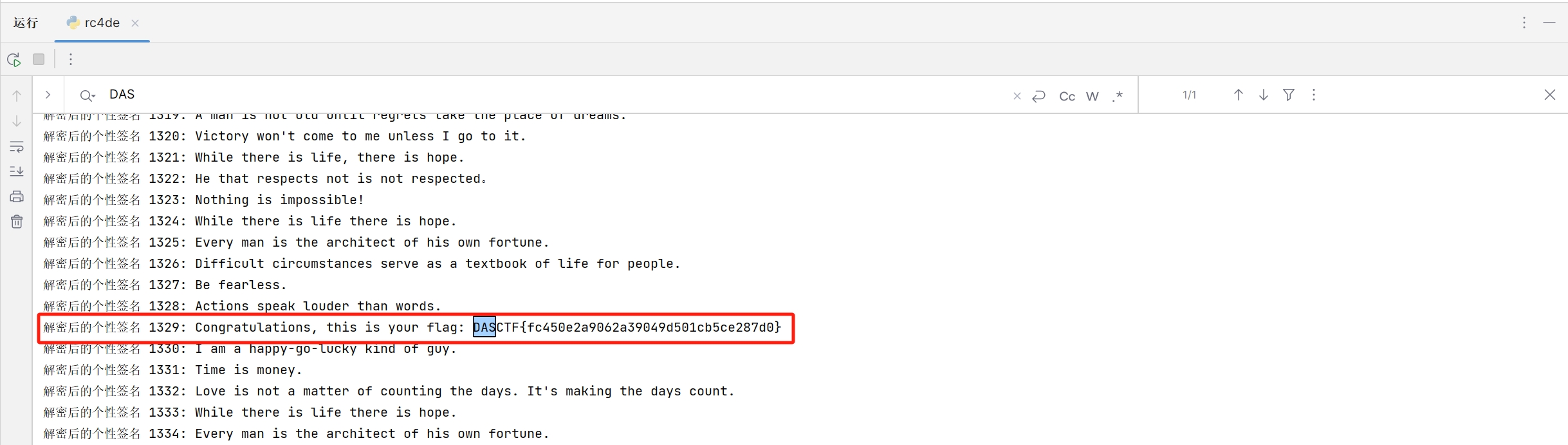
很遗憾比赛的时候没有做出来,主要是平常对AES-EAX加密模式基本上没什么了解,导致解密脚本写的有些问题,数据没有正常解密出来
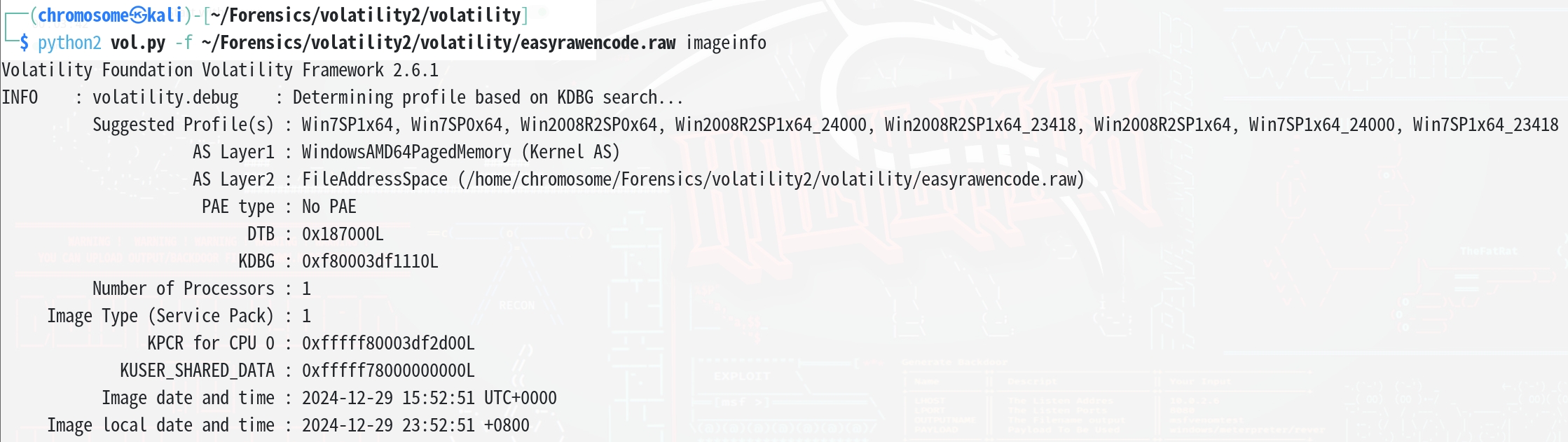
题目给了内存,先确定一下profile
1
| python2 vol.py -f ~/Forensics/volatility2/volatility/easyrawencode.raw imageinfo
|
然后查找一下可疑文件
1
| python2 vol.py -f ~/Forensics/volatility2/volatility/easyrawencode.raw filescan | grep -E 'txt|png|jpg|gif|zip|rar|7z|pdf|doc'
|
我们可以发现一个名为encrypted_data.zip的压缩包
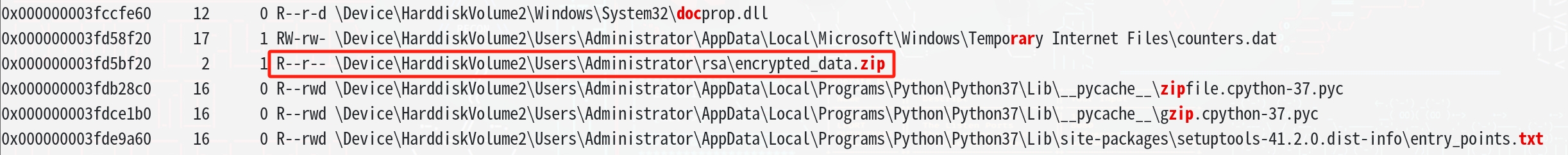
我们现在其实可以大概确定题目的考察方向了,利用一个加密算法加密了一些数据,然后我们需要在内存中找到加密算法的参数,然后对encrypted_data进行解密
现在我们重新进行文件扫描,但是给路径限定到存在rsa的路径
1
| python2 vol.py -f ~/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 filescan | grep -i "rsa"
|
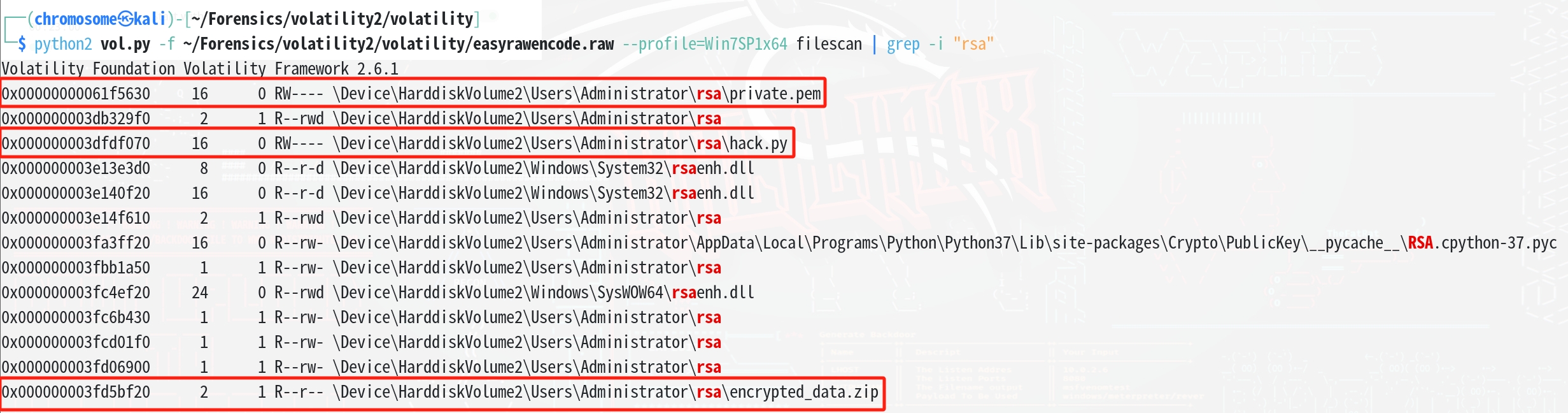
提取红框中的三个文件
1
2
3
4
5
| python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 dumpfiles -Q "0x000000003fd5bf20" --dump-dir=./
python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 dumpfiles -Q "0x00000000061f5630" --dump-dir=./
python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 dumpfiles -Q "0x000000003dfdf070" --dump-dir=./
|
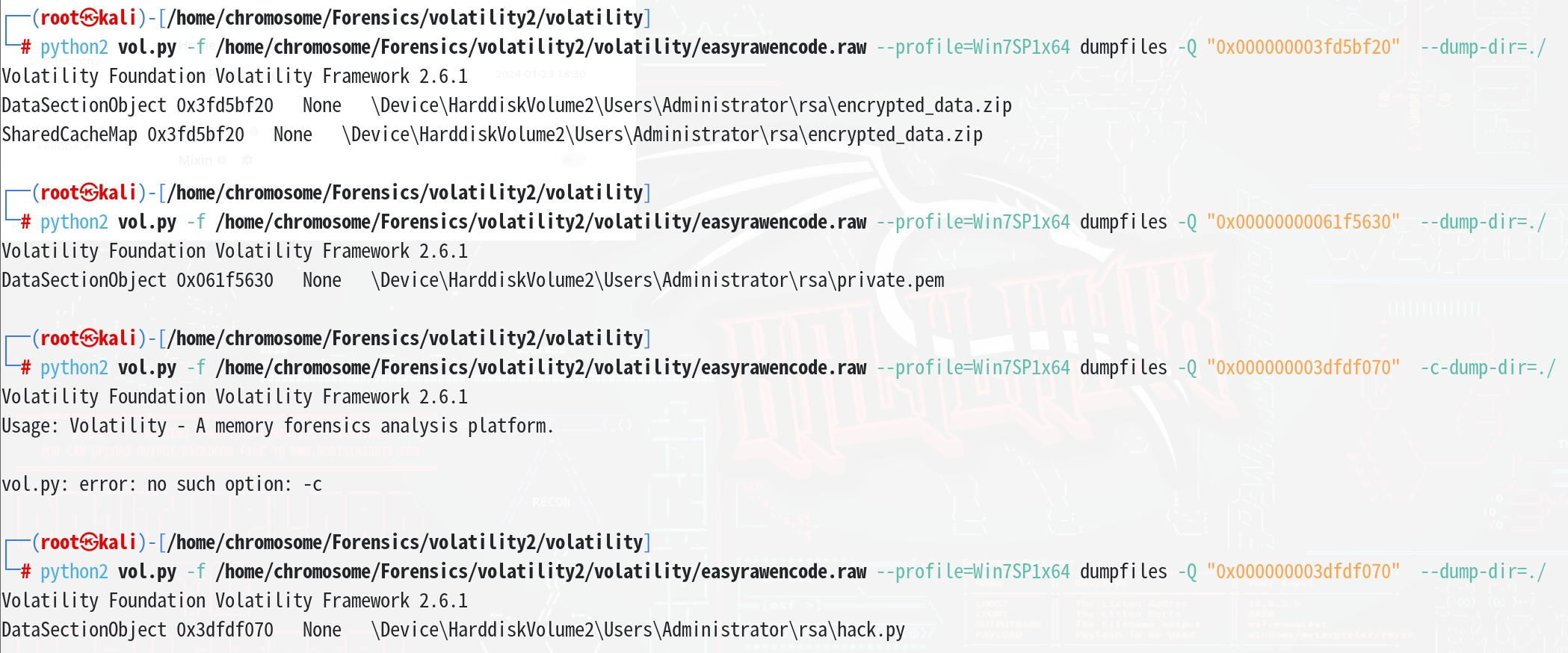
我们看一下hack.py的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| import os
import hashlib
from Crypto.Cipher import AES, PKCS1_OAEP
from Crypto.PublicKey import RSA
hackkey = os.getenv('hackkey')
if not hackkey:
raise ValueError("Environment variable 'hackkey' is not set")
with open('private.pem', 'r') as f:
private_key = RSA.import_key(f.read())
public_key = private_key.publickey().export_key()
aes_key = hashlib.sha256(hackkey.encode()).digest()
with open('data.csv', 'rb') as f:
data = f.read()
cipher_aes = AES.new(aes_key, AES.MODE_EAX)
ciphertext, tag = cipher_aes.encrypt_and_digest(data)
cipher_rsa = PKCS1_OAEP.new(RSA.import_key(public_key))
enc_aes_key = cipher_rsa.encrypt(aes_key)
with open('encrypted_data.bin', 'wb') as f:
f.write(ciphertext)
print(enc_aes_key.hex())
print(cipher_aes.nonce.hex())
print(tag.hex())
|
其实整个加密逻辑还是很清晰的,下面是对hack.py的整个流程的解释:
- 首先利用环境变量
hackkey派生了AES的加密密钥
- 利用AES-EAX模式对data.csv进行加密,返回密文和消息认证码
- 然后利用
private.pem导出公钥对我们的AES密钥进行加密
- 在python控制台中输出加密后的AES秘钥
enc_aes_key,EAX的随机数nonce,消息认证码tag
我们跟进Crypto.Cipher库中EAX模式的类可以发现解密中存在两个方法:
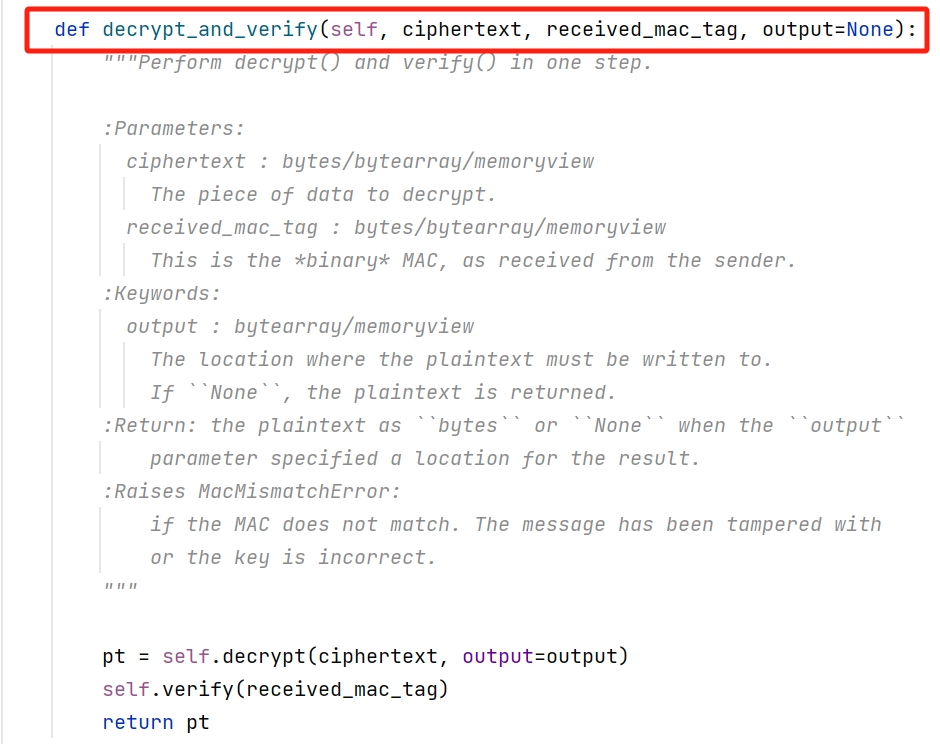
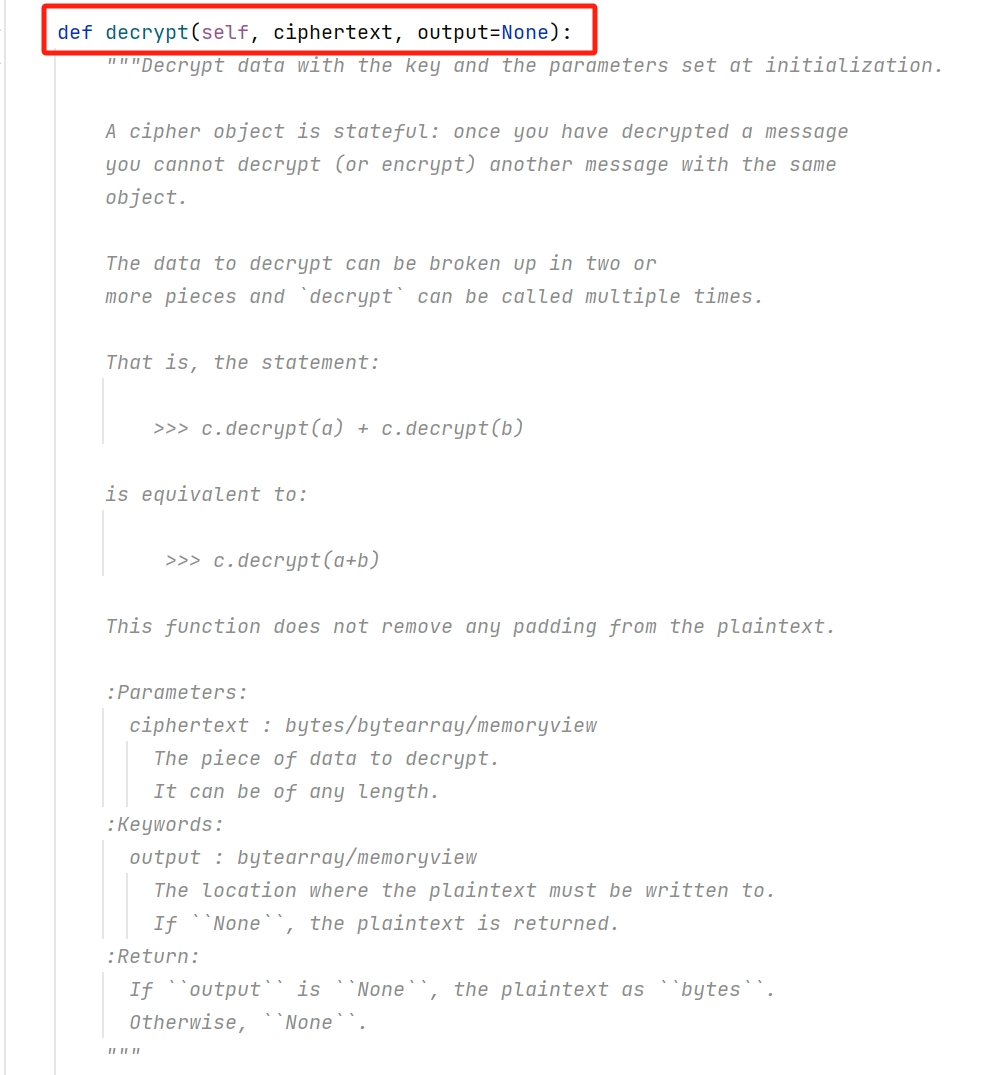
注:nonce需要在实例化EAX模式类的时候传入
那么我们可以得知,需要解密出我们的data.csv我们仅需要hackkey,nonce,encrypted_data.bin即可,其他的均为冗余的。
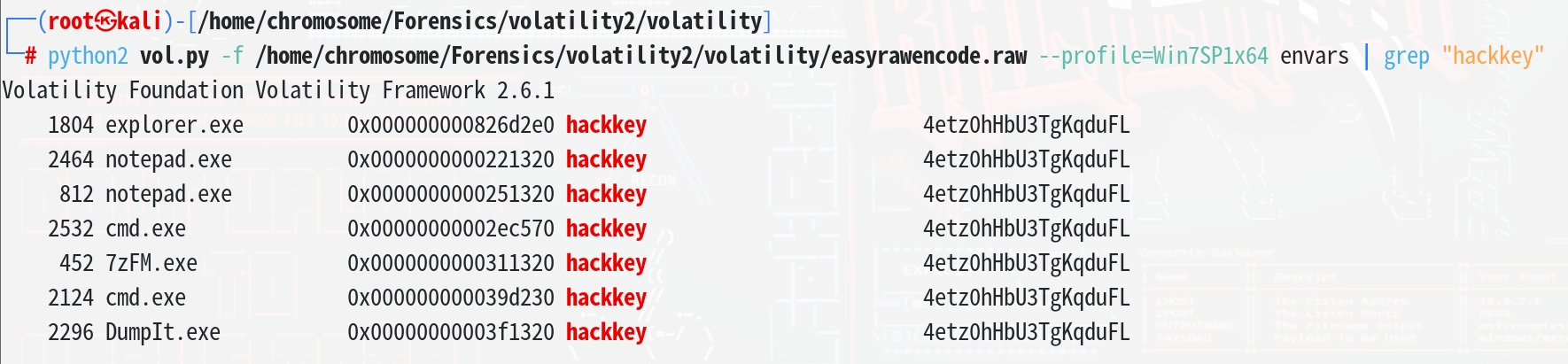
在环境变量中读取hackkey
1
2
3
| python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 envars | grep "hackkey"
4etz0hHbU3TgKqduFL
|
观察hack.py的运行方式
1
| python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 cmdscan
|
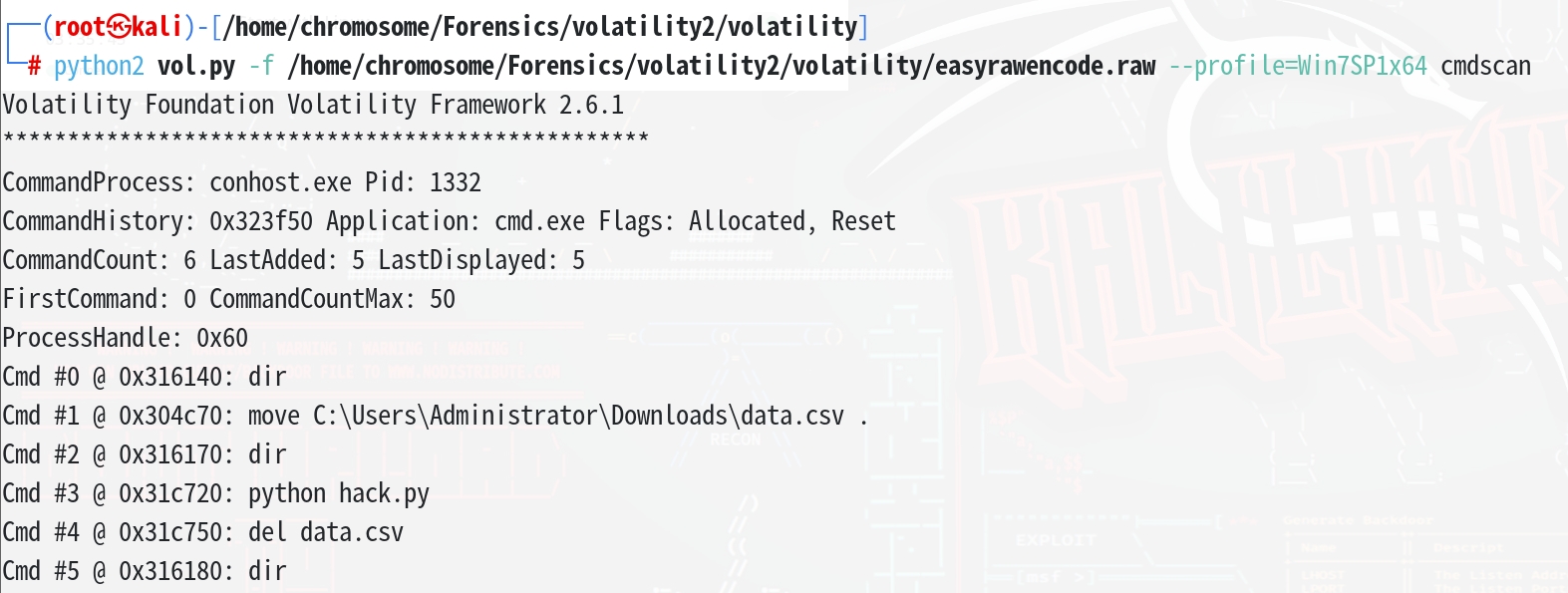
由上图得知hack.py在命令行中运行,那么我们就能读出运行后在命令行中留下的输出
1
| python2 vol.py -f /home/chromosome/Forensics/volatility2/volatility/easyrawencode.raw --profile=Win7SP1x64 consoles
|
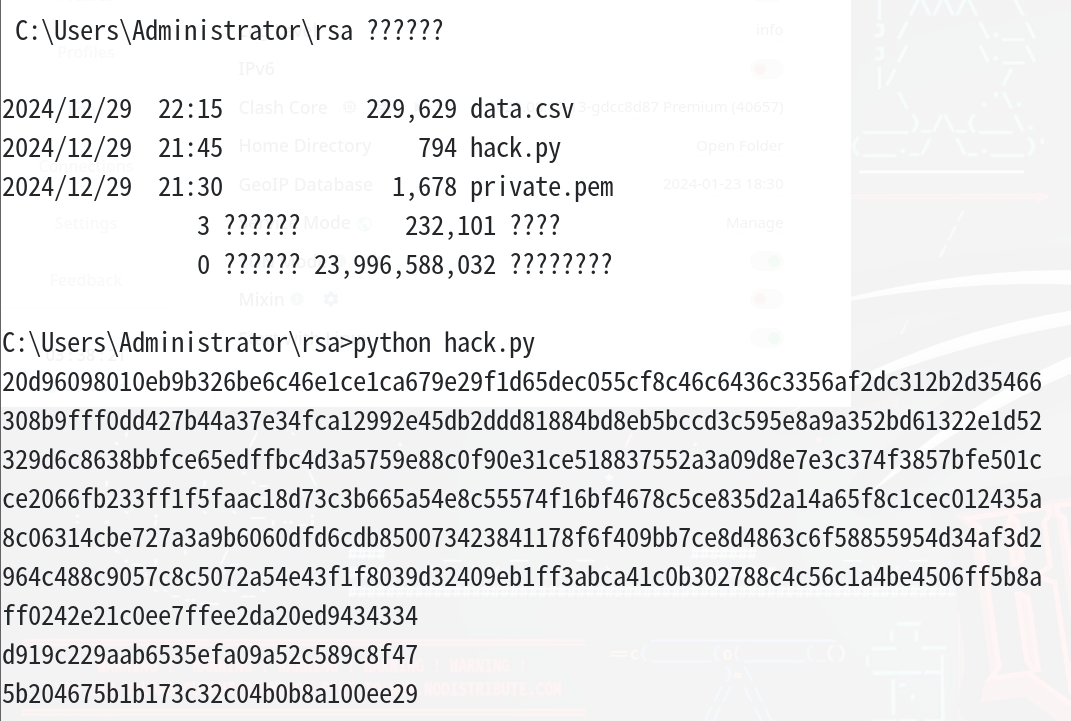
数据如下
1
2
3
4
5
6
7
8
9
| 20d96098010eb9b326be6c46e1ce1ca679e29f1d65dec055cf8c46c6436c3356af2dc312b2d35466
308b9fff0dd427b44a37e34fca12992e45db2ddd81884bd8eb5bccd3c595e8a9a352bd61322e1d52
329d6c8638bbfce65edffbc4d3a5759e88c0f90e31ce518837552a3a09d8e7e3c374f3857bfe501c
ce2066fb233ff1f5faac18d73c3b665a54e8c55574f16bf4678c5ce835d2a14a65f8c1cec012435a
8c06314cbe727a3a9b6060dfd6cdb850073423841178f6f409bb7ce8d4863c6f58855954d34af3d2
964c488c9057c8c5072a54e43f1f8039d32409eb1ff3abca41c0b302788c4c56c1a4be4506ff5b8a
ff0242e21c0ee7ffee2da20ed9434334
d919c229aab6535efa09a52c589c8f47
5b204675b1b173c32c04b0b8a100ee29
|
接下来直接用nonce和hackkey解密就行了,脚本如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| from Crypto.Cipher import AES
import hashlib
hackkey = "4etz0hHbU3TgKqduFL"
nonce = bytes.fromhex('d919c229aab6535efa09a52c589c8f47')
with open('encrypted_data.bin', 'rb') as f:
ciphertext = f.read()
aes_key = hashlib.sha256(hackkey.encode()).digest()
cipher_aes = AES.new(aes_key, AES.MODE_EAX, nonce=nonce)
data = cipher_aes.decrypt(ciphertext)
with open('data.csv', 'wb') as f:
f.write(data)
print("成功解密出data.csv")
|
使用notepad打开解密后的文件
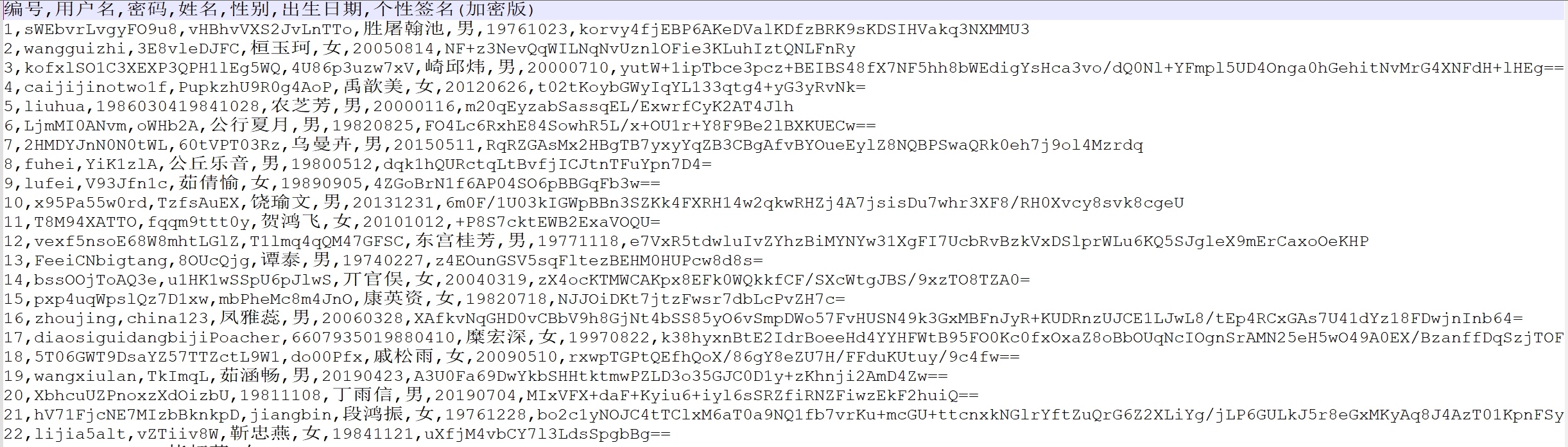
接下来就是确定个性签名的加密算法即可,在常见带key解密中尝试,确定RC4,写脚本解密即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| import csv
import base64
from Crypto.Cipher import ARC4
def rc4_decrypt(key, ciphertext):
cipher = ARC4.new(key.encode('utf-8'))
decrypted = cipher.decrypt(ciphertext)
return decrypted.decode('utf-8', errors='ignore')
def decrypt_signatures(csv_file):
with open(csv_file, newline='', encoding='utf-8') as csvfile:
reader = csv.reader(csvfile)
headers = next(reader)
decrypted_signatures = []
for row in reader:
password = row[2]
encrypted_signature_base64 = row[6]
encrypted_signature = base64.b64decode(encrypted_signature_base64)
decrypted_signature = rc4_decrypt(password, encrypted_signature)
decrypted_signatures.append(decrypted_signature)
return decrypted_signatures
csv_file = 'data.csv'
decrypted_signatures = decrypt_signatures(csv_file)
for i, signature in enumerate(decrypted_signatures):
print(f"解密后的个性签名 {i + 1}: {signature}")
|